Introduction
In networking, a DMZ (Demilitarized Zone) is a network segment that is designed to provide an additional layer of security between the internal network and the public Internet. A DMZ typically contains servers and services that are accessible from the Internet, but are segregated from the internal network to prevent unauthorized access to sensitive information.
Description
Cisco ASA (Adaptive Security Appliance) is a firewall and security device that provides network security services such as firewall, VPN, intrusion prevention, and content security. It also supports the creation of DMZ networks.
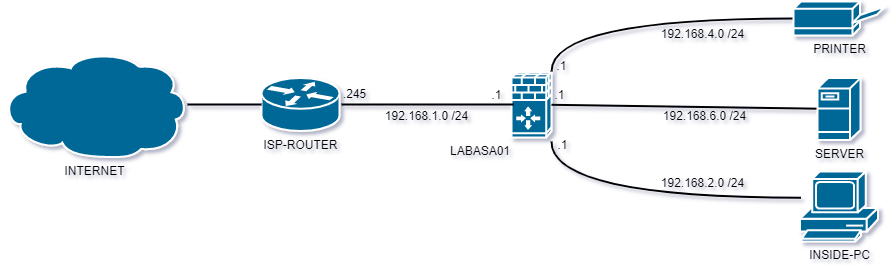
To create a DMZ using Cisco ASA, you need to configure the firewall to create a separate network segment that is physically isolated from the internal network and accessible from the Internet. The DMZ is usually created using a third interface on the firewall, which is configured with a separate subnet.
Once the DMZ interface is configured, you can then configure access control policies that allow or deny traffic between the DMZ, internal network, and the Internet. For example, you may allow certain types of traffic to flow from the Internet to the DMZ, such as HTTP or HTTPS traffic for web servers, while denying all other types of traffic.
A DMZ on a Cisco ASA is a network segment that is designed to provide an additional layer of security and is physically isolated from the internal network. It is typically used to host public-facing servers and services, such as web servers or email servers, that need to be accessible from the Internet while maintaining a high level of security.

0 Comments