Introduction
Cisco ASA (Adaptive Security Appliance) provides security by inspecting incoming and outgoing traffic and blocking unauthorized access. It is a stateful firewall that monitors incoming and outgoing network traffic and enforces security policies. Make sure to activate the "Security Plus" license to unlock more functionalities. Some of the key features of the Cisco ASA include:
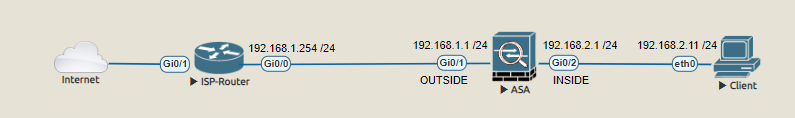
Topology
This topology describes connectivity to the internet via a home-router provided by an internet service provider. The ISP-router in this design offers a private network (192.168.1.0 /24). Most users at home connect their clients (notebooks, TVs, smartphones, etc.) directly to the home-router and receive an IP address from the built in DHCP server. The clients communicate to the internet by using the gateway (192.168.1.254 for this example). To add more security, the ASA (Adaptive Security Appliance) will enable the use of more subnets, inspect the incoming communication and translate the IP addresses of all clients to an IP address used by the firewall (port address translation). The CLI output below shows the device inventory, software version and shows that the device is running in router mode.
show inventory
ciscoasa# show inventory
Name: "Chassis", DESCR: "ASA 5505 Adaptive Security Appliance"
PID: ASA5505 , VID: V12 , SN: XXXXXXXXX
show version
ciscoasa# show version
Cisco Adaptive Security Appliance Software Version 9.1(7)32
Device Manager Version 7.12(1)
Compiled on Tue 04-Sep-18 08:37 by builders
System image file is "disk0:/asa917-32-k8.bin"
Config file at boot was "startup-config"
ciscoasa up 1 hour 27 mins
Hardware: ASA5505, 512 MB RAM, CPU Geode 500 MHz,
Internal ATA Compact Flash, 2048MB
BIOS Flash M50FW016 @ 0xfff00000, 2048KB
Encryption hardware device : Cisco ASA-5505 on-board accelerator (revision 0x0)
Boot microcode : CN1000-MC-BOOT-2.00
SSL/IKE microcode : CNlite-MC-SSLm-PLUS-2.08
IPSec microcode : CNlite-MC-IPSECm-MAIN-2.09
Number of accelerators: 1
0: Int: Internal-Data0/0 : address is 0000.0000.0000, irq 11
1: Ext: Ethernet0/0 : address is 0000.0000.0000, irq 255
2: Ext: Ethernet0/1 : address is 0000.0000.0000, irq 255
3: Ext: Ethernet0/2 : address is 0000.0000.0000, irq 255
4: Ext: Ethernet0/3 : address is 0000.0000.0000, irq 255
5: Ext: Ethernet0/4 : address is 0000.0000.0000, irq 255
6: Ext: Ethernet0/5 : address is 0000.0000.0000, irq 255
7: Ext: Ethernet0/6 : address is 0000.0000.0000, irq 255
8: Ext: Ethernet0/7 : address is 0000.0000.0000, irq 255
9: Int: Internal-Data0/1 : address is 0000.0000.0000, irq 255
10: Int: Not used : irq 255
11: Int: Not used : irq 255
Licensed features for this platform:
Maximum Physical Interfaces : 8 perpetual
VLANs : 20 DMZ Unrestricted
Dual ISPs : Enabled perpetual
VLAN Trunk Ports : 8 perpetual
Inside Hosts : Unlimited perpetual
Failover : Active/Standby perpetual
Encryption-DES : Enabled perpetual
Encryption-3DES-AES : Enabled perpetual
AnyConnect Premium Peers : 2 perpetual
AnyConnect Essentials : Disabled perpetual
Other VPN Peers : 25 perpetual
Total VPN Peers : 25 perpetual
Shared License : Disabled perpetual
AnyConnect for Mobile : Disabled perpetual
AnyConnect for Cisco VPN Phone : Disabled perpetual
Advanced Endpoint Assessment : Disabled perpetual
UC Phone Proxy Sessions : 2 perpetual
Total UC Proxy Sessions : 2 perpetual
Botnet Traffic Filter : Disabled perpetual
Intercompany Media Engine : Disabled perpetual
Cluster : Disabled perpetual
This platform has an ASA 5505 Security Plus license.
Serial Number: XXX
Running Permanent Activation Key: XXX
Configuration register is 0x1
Configuration last modified by enable_15 at 19:45:47.989 UTC Mon Jan 30 2023
ciscoasa#
enable
ciscoasa>
ciscoasa> enable
Password:
ciscoasa#
no firewall transpartent
ciscoasa# configure terminal
ciscoasa(config)# no firewall transparent
ciscoasa(config)# end
ciscoasa#
ciscoasa# show firewall
Firewall mode: Router
ciscoasa#

0 Comments