Introduction
The Firepower firewall provides security by inspecting incoming and outgoing traffic and blocking unauthorized access. It is a stateful firewall that monitors incoming and outgoing network traffic and enforces security policies.
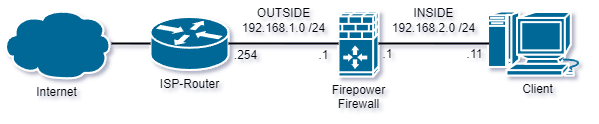
Topology
In this topology connectivity to the internet is possible via a home-router provided by an internet service provider. The ISP-router in this design offers a private network (192.168.1.0 /24). Most users at home connect their clients (notebooks, TVs, smartphones, etc.) directly to the home-router and receive an IP address from the built in DHCP server. The clients communicate to the internet via the gateway (192.168.1.254 for example). To add more security, the firewall will<br /> enable the use of more subnets, inspect the incoming communication and translate the IP addresses of all clients to an IP address used by the firewall (port address translation). The CLI output below shows the device inventory, software version and shows that the device is running in router mode.
show inventory
Name: "module 0", DESCR: "Firepower 1010 Appliance, Desktop, 8 GE, 1 MGMT"
PID: FPR-1010 , VID: V01 , SN: ############
show version
LABFW01# show version
Boot Loader version: 1.0.05
System version: 2.6(1.133)
Service Manager version: 2.6(1.133)
LABFW01#

0 Comments