Introduction
WLAN stands for Wireless Local Area Network. It refers to a type of wireless network that allows devices within a specific area to connect and communicate with each other wirelessly. A WLAN is commonly used to provide local network connectivity in homes, offices, schools, airports, cafes, and other public or private spaces. Key aspects of a WLAN include:
Advantages of WLANs include:
It’s worth noting that WLANs have certain limitations, including limited range compared to wired networks, susceptibility to signal interference, and potential security vulnerabilities. However, continuous advancements in Wi-Fi technology and security measures aim to address these challenges and enhance the performance and reliability of WLANs.
Standards Organizations
There are three main organizations that establish standards in the wireless networking industry:
802.11 Standards
802.11 is a set of standards developed by the Institute of Electrical and Electronics Engineers (IEEE) for wireless local area networks (WLANs). The 802.11 standards define the specifications for wireless communication, including data transfer rates, frequency bands, modulation techniques, and other aspects of wireless networking.
The table below explains the different technologies that were developed with the different 802.11 standards.
Radio Frequencies
Radio frequency (RF) refers to the range of electromagnetic frequencies within the electromagnetic spectrum that are commonly used for wireless communication and broadcasting. It encompasses frequencies ranging from a few kilohertz (kHz) to hundreds of gigahertz (GHz). 2.4 GHz & 5 GHz are commonly used for wireless communication, including Wi-Fi networks. A RF signal works as the medium to carry data, therefore RF signals are in the physical layer of the OSI model.
For wired networks cables are the physical medium. A RF signal works as the medium to carry data through the air, therefore RF signals are in the physical layer of the OSI model.
The image below shows the 2.4 GHz band:
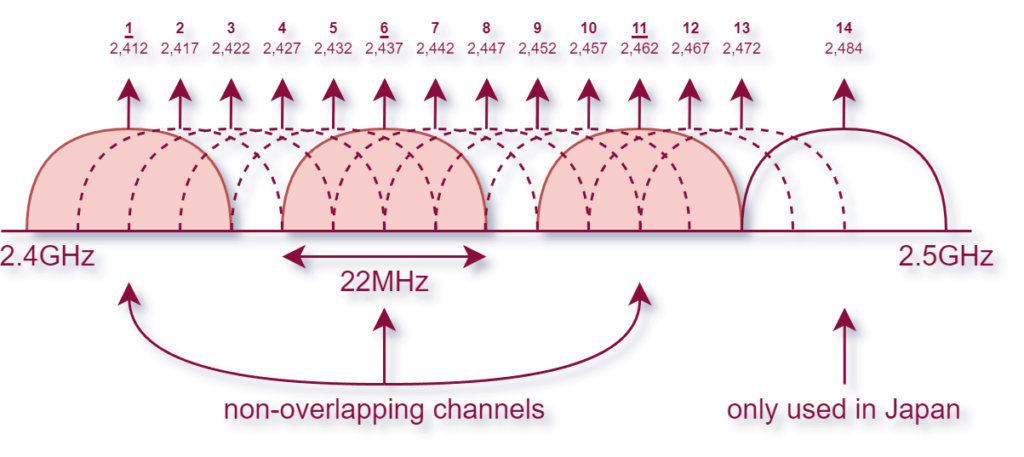
Each channel is 22 MHz wide. The non-overlapping channels in the 2.4 Ghz signal spektrum are 1, 6 & 11.
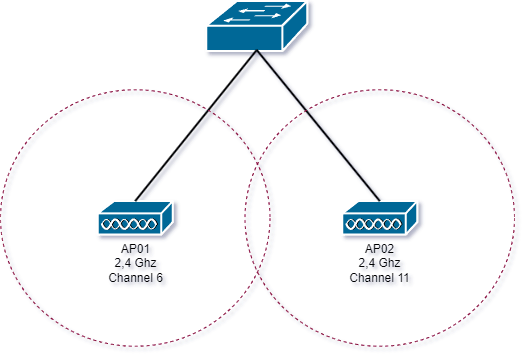
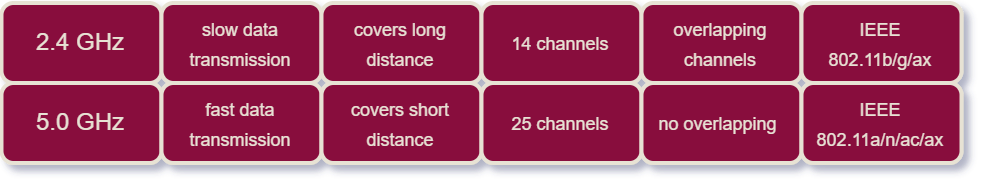
The tabe below shows the main differences between 2.4 & 5.0 GHz.
The image below shows the 5.0 GHz band:
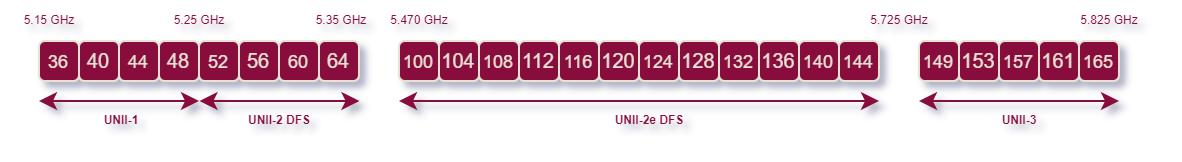
The 5.0GHz signal spectrum has no overlapping channels, therefore, making it easier to avoid interference.
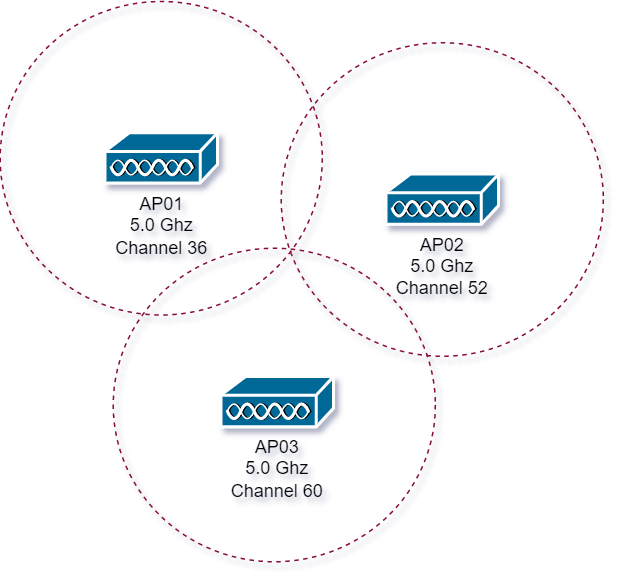
Radio Frequencies can naturally encounter different behaviours:
Collision Detection
Collision detection in wireless networks is a process that involves sensing and identifying when multiple devices attempt to transmit data simultaneously on the same wireless channel, resulting in a collision of signals. In wireless communication, collisions occur due to the shared nature of the wireless medium, where multiple devices contend for access to the channel. CSMA/CD (Carrier Sense Multiple Access with Collision Detection) and CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) are two different protocols used in network communication to manage how devices access the network medium.
WLANs operate in a half-duplex mode, which means that devices connected to the network can either transmit or receive data at any given time, but not both simultaneously. This is in contrast to full-duplex communication, where devices can both transmit and receive data simultaneously.
Electromagnetic Spectrum
The electromagnetic spectrum refers to the range of all possible electromagnetic waves, which are forms of energy that propagate through space in the form of oscillating electric and magnetic fields. It encompasses a wide range of frequencies and wavelengths, from low-frequency waves with long wavelengths to high-frequency waves with short wavelengths.
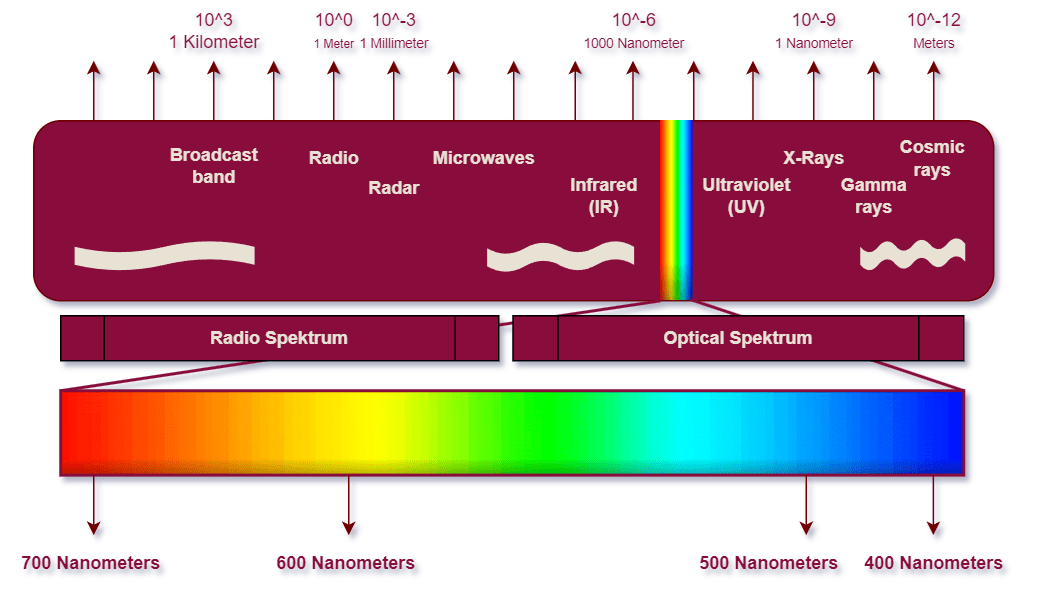
The electromagnetic spectrum encompasses a vast range of frequencies and wavelengths. At one end, it includes extremely low-frequency (ELF) waves and radio waves with long wavelengths and low frequencies. In the middle, it encompasses microwaves, infrared radiation, visible light (which is the narrow portion visible to the human eye), ultraviolet radiation, X-rays, and at the highest frequencies, gamma rays with short wavelengths and high frequencies.
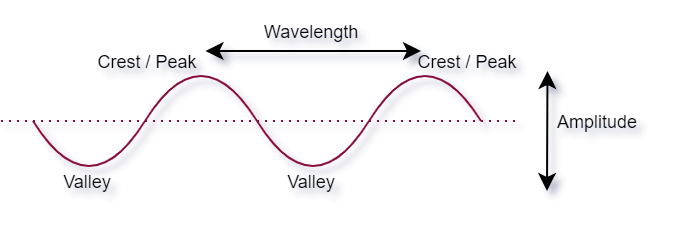
Wavelength
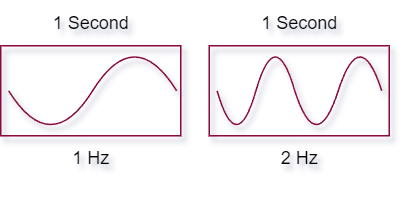
A wavelength refers to the distance between two consecutive points in a wave that exhibit the same phase and pattern. In a wave, there are specific points known as peaks and valleys that are relevant to understanding the concept of wavelength.
1 Hz refers to a frequency of one cycle per second. The unit “Hz” stands for hertz, which is the standard unit of frequency in the International System of Units (SI). Therefore, a cycle that occurs 500 times in a second is measured as 500 Hz.
Decibel
The decibel (dB) is a logarithmic unit used to express the relative intensity or power of a signal, sound, or measurement. It is widely used in various fields, including acoustics, telecommunications, electronics, and physics. Here are some key points about the decibel:
The received signal strength of both PCs differs by 10 decibels:
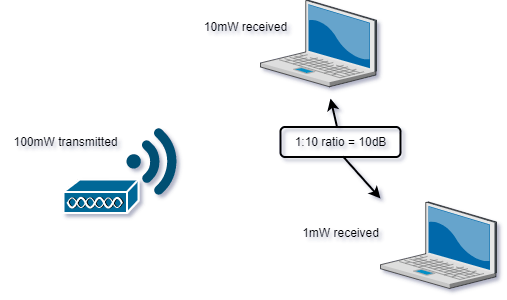
Decibel is used to measure the difference in power values. 3 dB doubles the strength of a reference signal, 10 dB multiply the strength of a reference signal by ten.
RSSI
RSSI stands for Received Signal Strength Indicator. It is a measurement used in wireless networks to quantify the strength of a received radio signal. RSSI indicates the power level of the signal that a device, such as a smartphone, laptop, or wireless access point, receives from another device, typically a wireless router or access point.
Wireless Topologies
Wireless networks can be designed in various different topologies:
AP Modes
Different Access Point modes offer specific functionalities and applications, enabling versatile wireless network configurations to suit different use cases and requirements. The list below shows the common modes for WLAN APs.
Antennas
Antennas are used to transmit the signal into the air, and the signal must be radiated with sufficient power to be received by receivers. There are different types of antennas and installations that are used in different use cases.

The two main categories of antennas are "omnidirectional", and "directional". The image above shows the signal of an omnidirectional antenna from the top and from the side. The table below shows different Cisco WLAN access points using different types of antennas. Modern access points feature multiple antennas for a technology known as Multiple-Input Multiple-Output (MIMO), which significantly enhances wireless network performance and reliability. MIMO takes advantage of the spatial dimension to improve data throughput, increase network coverage, and mitigate signal interference.
The images below show how the signal spreads when using different types of antennas. Antenna strength is measured as a reference to an isotropic rediator. dBi is a measurement of gain as compared to an isotropic radiator measured at the strongest point (focal point) of the signal.
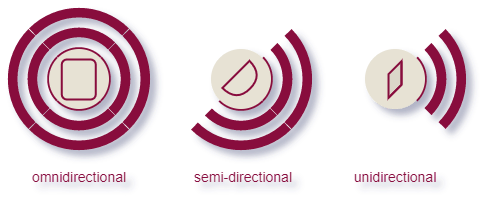
Radiation Patterns
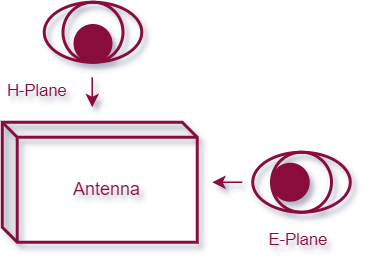
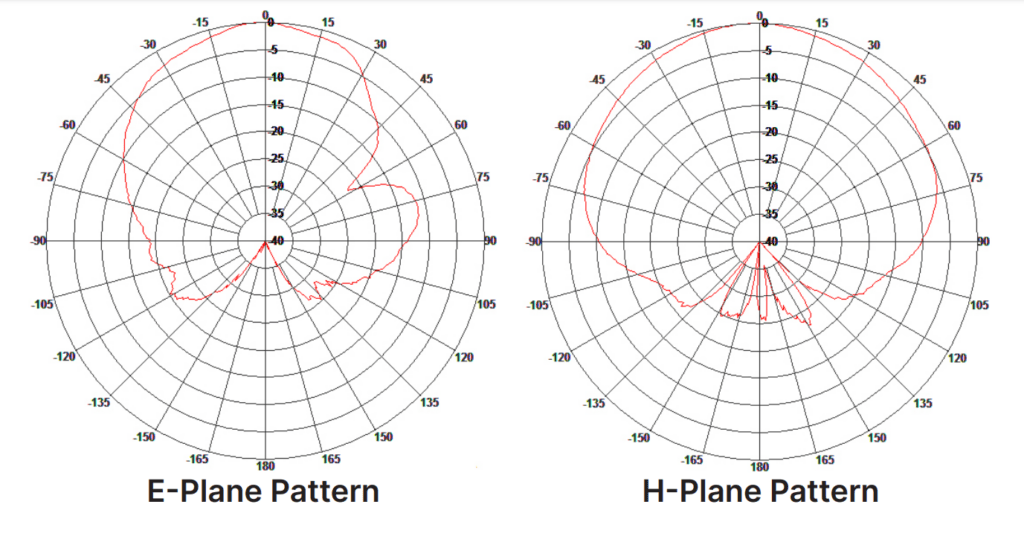
H-plane (Horizontal Plane) and E-plane (Vertical Plane) are terms used in the context of antenna radiation patterns to describe the two principal planes in which the antenna's electromagnetic energy is distributed.
The image below shows the radiation pattern of a patch antenna form the vertical, and the horizontal view point. The antenna could be classified as an semi-directional antenna because of the broad signal pattern. These charts contain no information about distance, only the shape of the signal.
The H-Plane describes the signal pattern viewed from the top, and the E-Plane describes the signal pattern viewed from the side while the antenna is placed in the middle of the radiation circle.
SSID
SSID stands for Service Set Identifier. It is a unique name assigned to a wireless network to identify and differentiate it from other nearby networks in the same vicinity. The SSID is used to help devices, such as laptops, smartphones, and other Wi-Fi-enabled devices, identify and connect to the correct network.
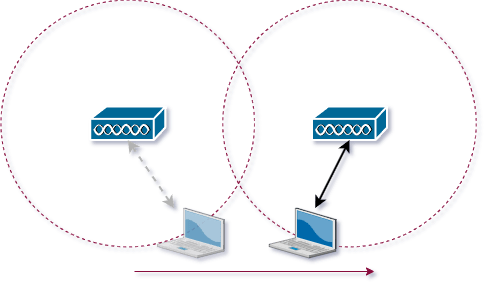
Roaming
Roaming in the context of wireless networking refers to the ability of a mobile device, such as a smartphone, laptop, or tablet, to seamlessly switch its connection from one wireless access point (AP) to another while maintaining an ongoing network session. This is particularly important in environments with multiple access points, such as a large office building, airport, or campus, where a single AP's coverage might not extend throughout the entire area.
Power over Ethernet
POE stands for Power over Ethernet. It is a technology that allows electrical power to be transmitted along with data over Ethernet cables, typically used to connect network devices such as wireless access points, IP cameras, and VoIP phones to a network. This eliminates the need for separate power cables, simplifying installations and improving flexibility.
The image below shows a POE network switch:

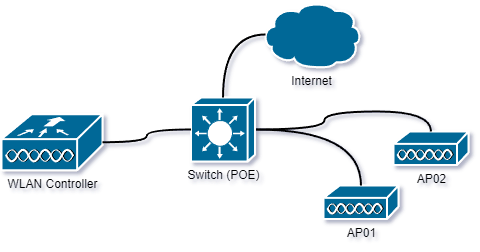
WLAN Controller
A Wireless LAN (WLAN) Controller is a central device used to manage and control a network of wireless access points (APs) in an enterprise or larger-scale wireless network deployment. It serves as a centralized point of control for configuring, monitoring, and managing various aspects of the wireless network infrastructure. Key functions and features of a WLAN Controller:
Security
Security in Wireless Local Area Networks (WLANs) is crucial to protect sensitive data, prevent unauthorized access, and maintain the integrity of the network. Various security measures are employed to ensure the confidentiality, authenticity, and availability of data in WLANs. Some key security aspects in WLANs include:
Authentication
Authentication is vital for preventing unauthorized access, data breaches, and malicious activities. It is the process of verifying the identity of a user, device, or system to ensure that the claimed identity is legitimate and authorized to access specific resources or services. It is essential to use the most up-to-date and secure protocols to safeguard wireless communication and prevent unauthorized access to sensitive data.
EAP
EAP, or Extensible Authentication Protocol, is a framework that defines various authentication protocols used in wireless networks, point-to-point (P2P) connections, and other network access scenarios. EAP itself is not a specific authentication method but rather a framework that allows for the use of different authentication protocols within its structure. EAP is commonly used in wireless networks, such as Wi-Fi networks, to secure the authentication process between a client (like a laptop or smartphone) and an authentication server. Some popular EAP methods include EAP-TLS (Transport Layer Security), EAP-PEAP (Protected Extensible Authentication Protocol), EAP-LEAP (Lightweight Extensible Authentication Protocol), and EAP-TTLS (Tunneled Transport Layer Security). There are several variations of EAP (Extensible Authentication Protocol), each designed to address specific security and authentication requirements.
Encryption
Encryption is a security process used to protect sensitive data by converting plain, readable information (plaintext) into an unreadable format (ciphertext). It ensures data confidentiality and integrity during transmission and storage, making it challenging for unauthorized individuals to access or manipulate the information.
Authentication Methods
Authentication methods are mechanisms used to verify the identity of devices or users attempting to connect to a Wi-Fi network. These authentication methods help ensure that only authorized users or devices gain access to the network and its resources. Several WLAN authentication methods exist, and they can be broadly categorized into the following types:
MAC-Filtering
MAC filtering, also known as MAC address filtering or Access Control List (ACL), is a security feature used in wireless networks to control device access based on the Media Access Control (MAC) addresses of their network interface cards (NICs). A MAC address is a unique identifier assigned to each network device, and it is hardcoded into the device's hardware.

0 Comments